Tool Arguments Encryption
Overview
Tool argument encryption protects sensitive data like Social Security Numbers, Credit Card Numbers, and other PII by encrypting specific fields before they’re sent to your server.
In this guide, you’ll learn to:
- Create and configure a custom credential with encryption enabled
- Generate RSA public/private key pairs
- Configure tools to encrypt specific argument fields
- Decrypt encrypted data on your server
Prerequisites
- A Vapi account with access to the dashboard
- OpenSSL or a similar tool for generating RSA keys
- A server endpoint that can receive and decrypt encrypted data
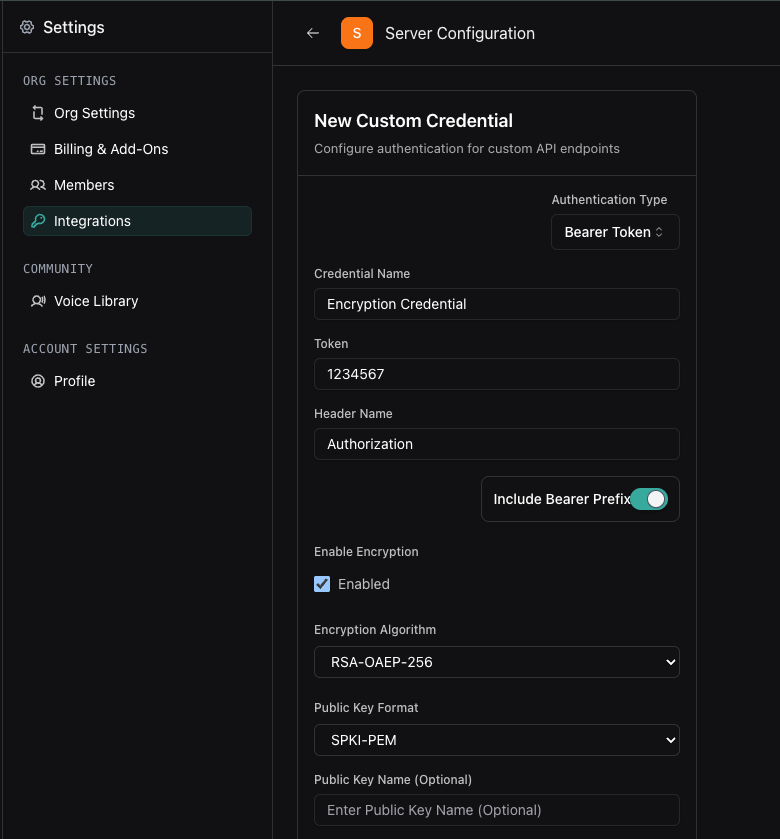
Create a custom credential with encryption
Navigate to the custom credentials page and enable encryption settings.
- Go to https://dashboard.vapi.ai/settings/integrations/custom-credential and click “Add Custom Credential”
- Check Enable Encryption
- Select RSA-OAEP-256 as the algorithm
- Select SPKI-PEM as the format
Generate RSA key pair
Use OpenSSL to generate a public/private key pair in PEM format.
Run this command in your terminal to generate both keys:
This creates two files:
private-key.pem- Keep this secure on your server for decryptionpublic-key.pem- Copy this to Vapi for encryption
Never share or commit your private key. Store it securely in your server’s environment variables.
Add public key to credential
Copy and paste your public key into the Vapi dashboard.
- Open
public-key.pemand copy the entire contents - Paste the public key PEM into the Public Key PEM field
- Click Save
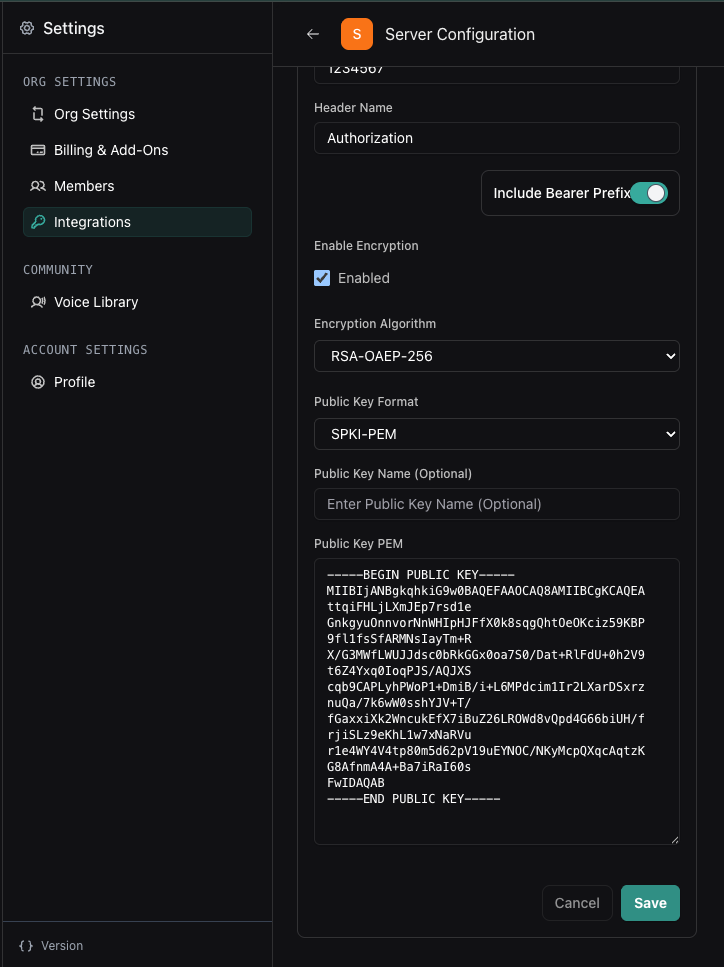
Your credential is now ready to use with encrypted tool arguments.
Select a tool to configure
Navigate to your tools and choose which tool should use encryption.
- Go to the Tools page
- Select an existing Custom Tool or API Request Tool
- Alternatively, create a new tool if needed
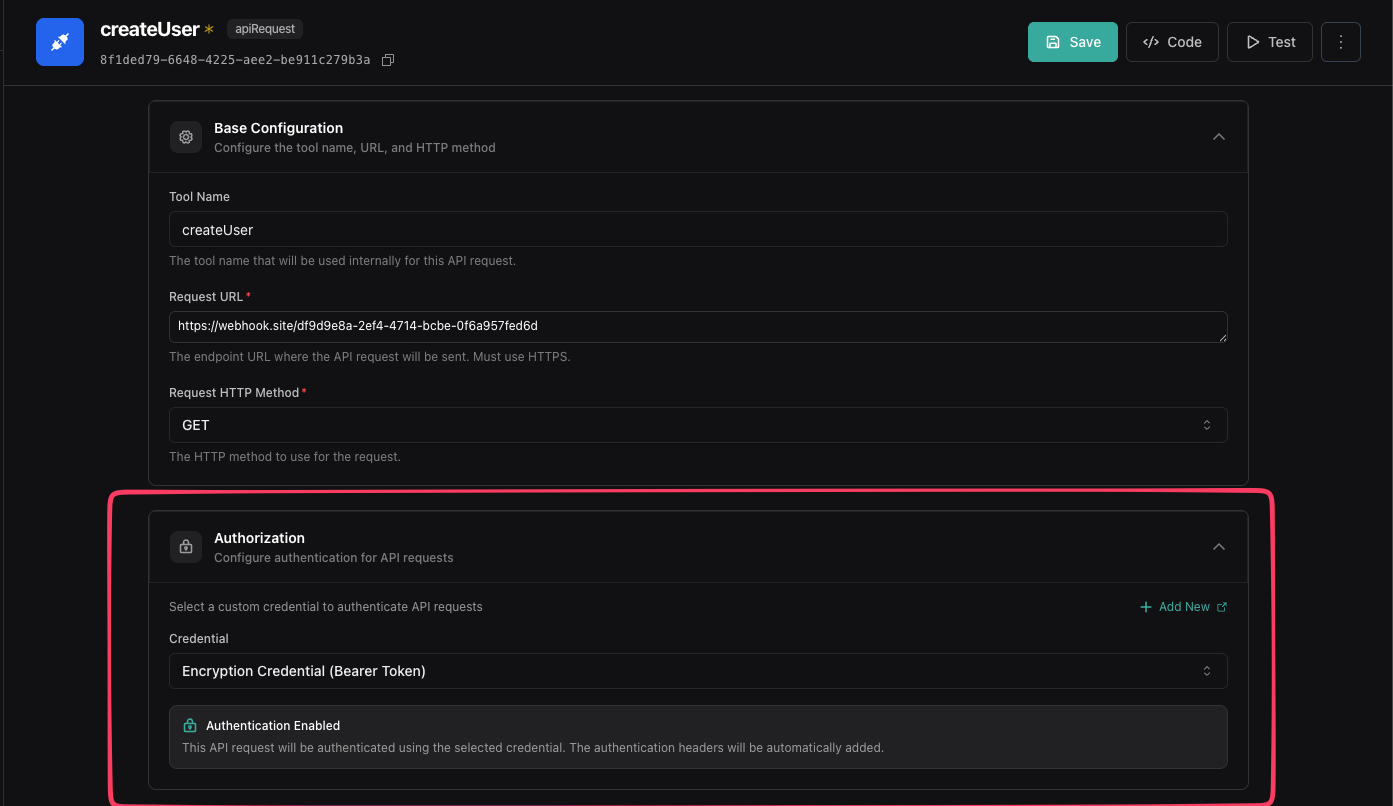
Configure credential and encryption settings
Link your encryption credential and specify which fields to encrypt.
- In the tool settings, find the Credential dropdown
- Select the credential you created in Step 1
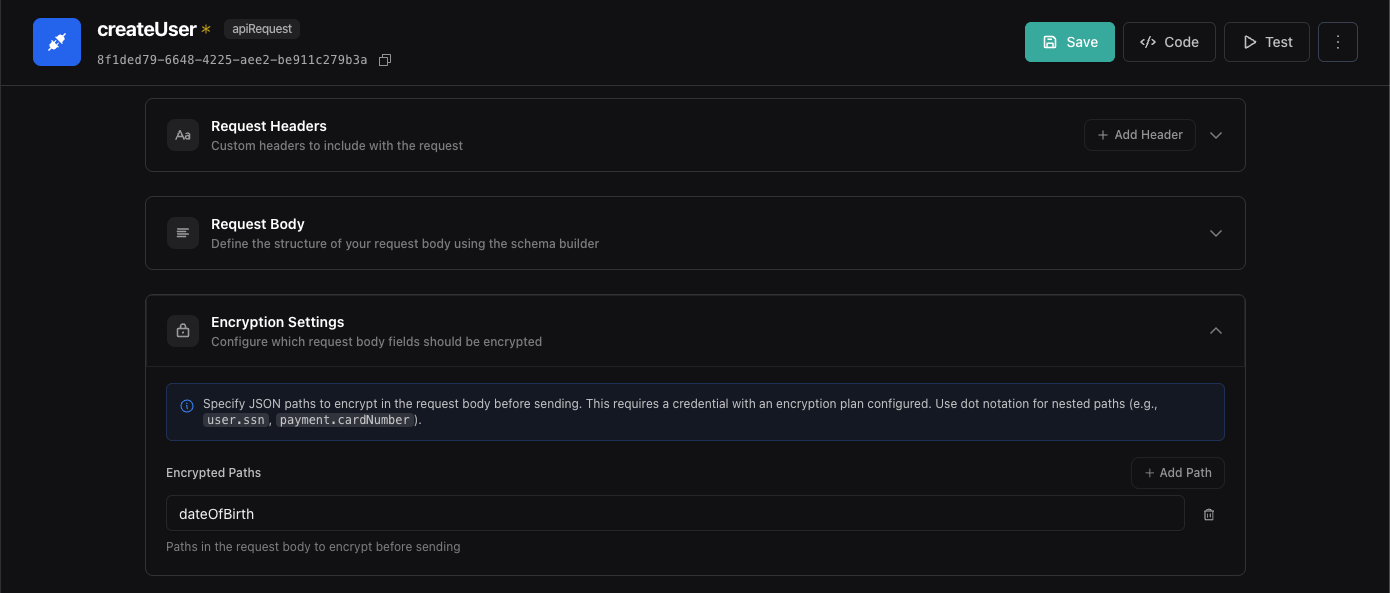
- Scroll to Encryption Settings
- Add the exact JSON paths to the arguments you want encrypted
Example JSON paths:
ssn- Encrypts thessnfieldpayment.cardNumber- Encrypts nested fields
JSON paths are relative to the tool’s argument structure. Only specified fields will be encrypted.
Save and test the configuration
Save your tool configuration and verify encryption works with a test call.
- Click Save to apply your changes
- Make a test call using an assistant with this tool
- Trigger the tool during the call
- Check your server logs to confirm encrypted data arrives
When your server receives the webhook, encrypted fields will appear as base64-encoded strings:
Security best practices
Follow these guidelines to maintain secure encryption:
- Never commit private keys - Use environment variables or secret management systems
- Rotate keys periodically - Generate new key pairs and update credentials regularly
- Encrypt selectively - Only encrypt fields that contain sensitive data to minimize overhead
- Validate decrypted data - Always validate and sanitize decrypted values before use
- Use HTTPS - Ensure your server endpoint uses HTTPS for transport security
Next steps
Now that you have tool argument encryption configured:
- Custom tools: Learn more about creating custom tools
- API request tools: Configure API request tools with encrypted arguments
- Server URLs: Set up secure server endpoints for receiving encrypted data